The Importance of a Strong Password.
As we navigate an increasingly connected world, the importance of a strong password intensifies. Every facet of our online interactions, from personal data storage and business communications to financial transactions and identification verifications, is safeguarded by passwords.
Are you one of the many using passwords such as ‘qwerty‘, ‘abcd‘, ‘12345‘, or simply ‘password‘? Such easily guessable combinations are cracked almost instantly, posing immense risks to your online security. Read on to discover the hazards of inadequate password choices and learn strategies for devising and maintaining strong, protective passwords.
A prevalent misstep is the repeated use of a single password across various online accounts. This practice is riddled with danger; a breach in one area can potentially unlock access to all others. The fallout from compromised passwords can be severe, potentially resulting in the loss of vital data, monetary resources, or even personal identity.
Remember, passwords are your initial shield against unauthorised digital intrusions. The sturdier they stand, the better protected you are from potential cyber threats.
The Benefits of a Strong Online Password.
In the vast expanse of the digital universe, a password is akin to a personal guardian. It stands as the primary barrier between our private information and potential cyber threats. Here’s why a strong online password is of paramount importance:
- Protection from Unauthorised Access: A robust password ensures that only you can access your accounts, be it email, social media, or financial platforms. It prevents outsiders from gaining unauthorised entry, thus safeguarding your personal and financial data.
- Shield Against Cyber Attacks: Weak passwords are easy prey for cybercriminals. Using techniques like brute force attacks, they can quickly crack simple passwords, leaving your accounts vulnerable. A complex password, on the other hand, is much harder to decipher.
- Guarding Personal Identity: Identity theft is a rising concern. Cybercriminals often seek personal details to impersonate others, leading to fraudulent activities. A strong password acts as a bulwark, ensuring your identity remains protected.
- Financial Security: Many online platforms linked to your financial details require passwords. Whether it’s online banking, shopping, or investment platforms, a potent password is crucial to prevent monetary theft.
- Maintaining Professional Integrity: For professionals and businesses, a breach can mean not just personal, but also client data loss. A resilient password ensures that sensitive business information and client details remain confidential.
- Promotion of Good Digital Hygiene: Adopting the practice of setting strong passwords fosters a mindset of security. It’s a foundational step in cultivating good digital habits, which also includes regular password updates and employing multi-factor authentication.
As we further immerse ourselves in the digital age, the strength of our passwords will play a decisive role in determining the safety of our online presence. Investing time in creating a solid password is a small yet crucial step in ensuring comprehensive online security.
Understanding the Vulnerability of Simplistic Passwords.
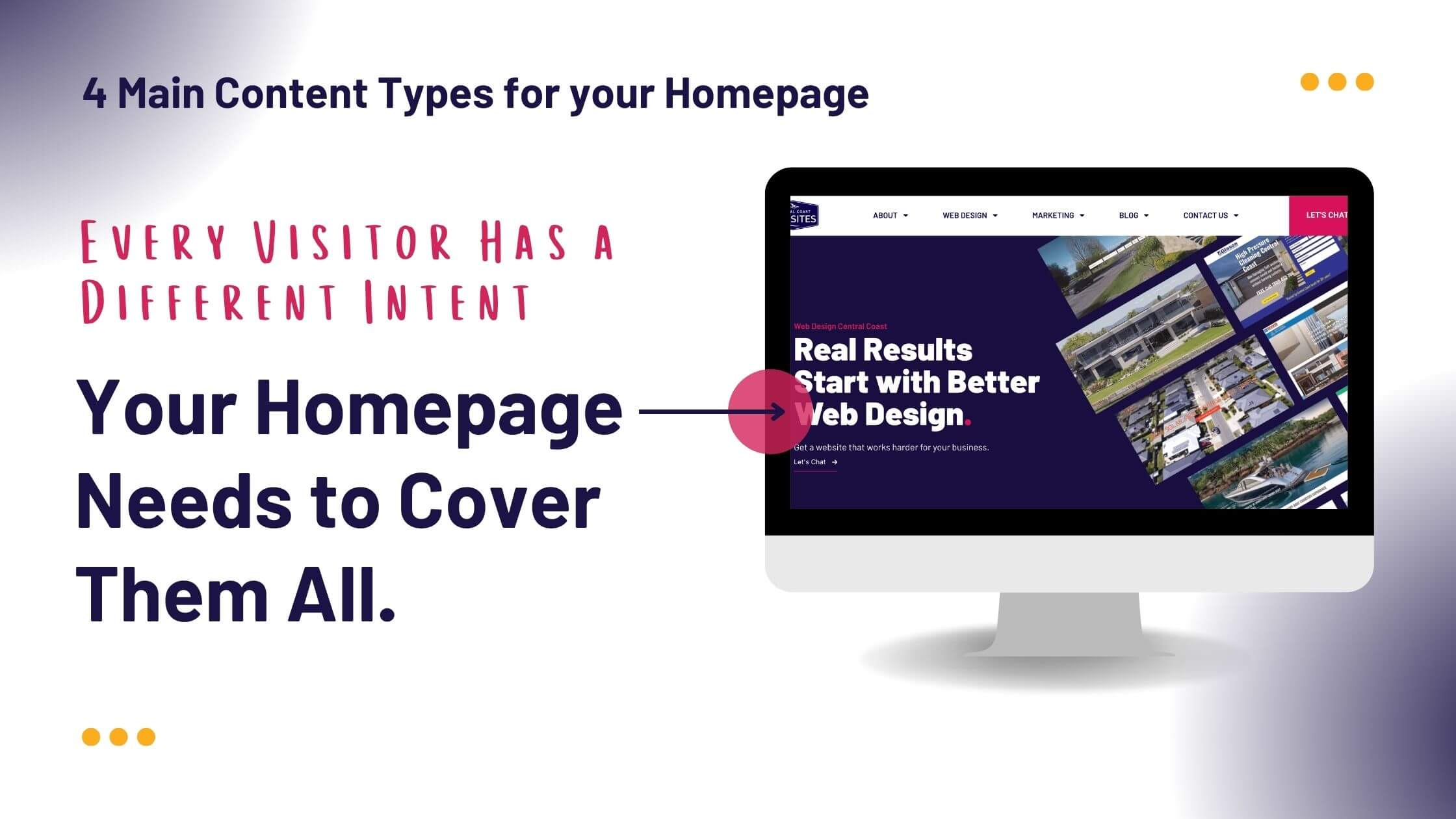
It’s astonishing, but true: many individuals continue to rely on passwords as basic as ‘123456’ or ‘abcd’. Such elementary passwords are a goldmine for cybercriminals, as depicted in the referenced image below from Patchstack.
The graphic reveals a startling fact: the password ‘123456’ can be deciphered in less than a second. Despite its vulnerability, it’s alarming that over 2.5 million users opt for this password. Recent studies we conducted show that while millennials exhibit higher awareness of potential digital security threats, their level of concern remains relatively low. This nonchalance can be attributed to their digital-native upbringing, making them perceive data breaches as unfortunate yet commonplace events. However, it’s crucial to emphasise that as technology increasingly intertwines with our daily lives, the ramifications of data breaches and cyber fraud intensify. One of the primary defences we have against such threats is fortifying our digital gatekeepers – our passwords. By choosing robust and unique passwords, we can significantly bolster our online security and protect our invaluable data.
Prioritising Password Strength:Your First Line of Online Defense
One of the most straightforward yet vital steps you can take to fortify your online security is establishing robust passwords. Such passwords act as formidable barriers, shielding your online accounts and devices from unauthorised intrusions.
Guidelines for Crafting a Formidable Password
- Diversify Your Characters: Incorporate a blend of numbers, symbols, and both uppercase and lowercase letters. Intermingling these unpredictably strengthens your password. For instance, consider substituting ‘o’ with ‘0’, ‘s’ with ‘$’, or ‘a’ with ‘@’.
- Length Equals Strength: A protracted password inherently offers more resistance against hacking attempts. Techniques like brute force attacks, where hackers deploy software to test every conceivable character combination, find it tougher to crack lengthier, intricate passwords.
- Steer Clear of Repetition: Deploying identical passwords for multiple accounts is a perilous practice. Should one account be compromised, all others sharing that password are instantly at risk. Endeavour to keep each password unique.
- Embrace Password Managers: These tools are invaluable in producing and storing robust passwords for all your accounts. Stored in a secure, encrypted vault, you can access them using a singular master password.
- Personal Isn’t Always Best: Many fall into the trap of using easily retrievable personal details like pet names, anniversaries, or favourite sports teams as passwords. This makes them more predictable and susceptible to being guessed.
- Refresh Regularly: Periodically updating your passwords enhances your online safety quotient.
Adhering to these guidelines not only ensures the protection of your website credentials but also bolsters the security of all your online engagements. In an era where digital threats are ever-evolving, having a formidable password is an essential first step in safeguarding your digital footprint.
The Importance of Strong Passwords: Safeguarding Your Digital Assets
In the digital age, the significance of a sturdy password cannot be overstated. It stands as the primary shield against unauthorised intrusions into your electronic domains, from personal accounts to vital business platforms.
A password, when intricately crafted and sufficiently elongated, presents a formidable challenge to potential hackers. Whether they employ brute force tactics, where every conceivable combination is tried, or sophisticated automated attacks, a complex password drastically reduces their chances of success. In essence, the intricacy of your password directly correlates with the level of protection it offers, acting as a robust barrier between your valuable data and cyber adversaries. By prioritising password strength, you’re investing in a foundational layer of defence for your digital assets and identity.
The Evolution of Password Management:Keychains and Password Managers
In our digital era, where countless accounts and services necessitate unique login credentials, remembering a myriad of complex passwords becomes a daunting task. Enter keychains and password protectors: these tools are designed to simplify and bolster online security. Keychains, like Apple’s iCloud Keychain, seamlessly store and fill in passwords across devices, ensuring users don’t have to recall every intricate detail. Similarly, password managers, such as LastPass or Dashlane, act as digital vaults. They not only store passwords but can also generate strong, random passwords for users, enhancing security. Encrypted with robust algorithms, these tools ensure that your credentials remain shielded from prying eyes. By centralising password management, they offer both convenience and an added layer of defence against potential cyber threats.
The New Frontiers of Security:Facial Recognition and Fingerprint Logins
The digital security landscape is constantly evolving, and one of the most notable advancements has been the integration of biometric authentication methods like facial recognition and fingerprint logins. These techniques harness unique physical attributes of users to grant access, making unauthorised breaches significantly more challenging. Facial recognition systems, utilised by devices like smartphones and security cameras, scan and match facial features against a stored template. Similarly, fingerprint logins rely on the distinct ridges and patterns of an individual’s fingerprint. Both methods offer a level of security that’s difficult to replicate or forge, unlike traditional passwords which can be guessed or hacked. Additionally, they provide users with the convenience of quick access without the need to remember complex passwords. However, as with all technologies, it’s crucial to ensure these systems are implemented with stringent security measures to prevent potential misuse or vulnerabilities.
Diverse Hacking Strategies Targeting Passwords.
In the shadowy underworld of cyberattacks, hackers employ a myriad of techniques to breach passwords and gain unauthorised access to accounts. The Brute Force Attack, is a methodical approach where every conceivable password combination is tested. Dictionary Attacks target passwords using a predefined list of common words or phrases, capitalising on the tendency of users to select easily memorable passwords. Phishing involves duping individuals into revealing their passwords, often through seemingly legitimate emails or web pages. Keylogging is a more covert approach where malicious software records a user’s keystrokes, capturing passwords as they’re typed. Credential Stuffing exploits individuals who reuse passwords across multiple platforms; once one account is breached, others become vulnerable. Finally, Rainbow Table Attacks use precomputed tables to reverse cryptographic hash functions and unearth passwords. With such a diverse arsenal at their disposal, the importance of robust password practices becomes all the more evident.
What is a Brute Force Attack?
A brute force attack can be likened to a cyber burglar trying every possible key in a massive keychain to unlock a door. Essentially, it involves methodically attempting all possible combinations of letters, numbers, and special characters until the correct one is found. This “brute force” approach might seem rudimentary, yet its simplicity is precisely what makes it a favoured strategy among hackers. Despite being an age-old tactic, it remains alarmingly effective. With the computational prowess of modern tools, even a seemingly complex password can be deciphered in mere seconds, as highlighted in the aforementioned table.
Understanding Dictionary Attacks.
A Dictionary Attack is a type of cyber assault where hackers attempt to gain unauthorised access by systematically entering every word from a predefined list, often extracted from dictionaries. Unlike brute force attacks, which try every possible combination of characters, dictionary attacks capitalise on the human propensity to use real words or common phrases as passwords. These attacks are especially effective against accounts secured with weak or commonly-used passwords. As technology has advanced, so has the sophistication of these attacks; hackers now often incorporate variations of words, adding numbers or symbols, to widen the net of potential matches. To counteract the threat posed by dictionary attacks, it’s crucial to use complex passwords that aren’t solely based on standard dictionary terms. Incorporating a mix of characters, numbers, and symbols can greatly enhance password security and resilience against such intrusions.
Phishing Attacks.
Phishing is a deceptive technique employed by cybercriminals to trick individuals into divulging sensitive information, often passwords. Typically executed through seemingly genuine emails, messages, or web links, phishing attacks lure unsuspecting users into entering their credentials on counterfeit websites or platforms. These fake sites are meticulously crafted to mimic the appearance of legitimate entities, be it banks, service providers, or popular online platforms, thereby gaining the trust of the target. Once the user inputs their information, the attacker captures it for malicious purposes. The sophistication of phishing schemes has grown over the years, with attackers employing more personalised tactics, such as spear-phishing, where the deception is tailored to a specific individual using gathered personal details. As phishing continues to evolve, it underscores the importance of vigilance and education in recognizing and avoiding potential traps in the digital landscape.
Keylogging.
Keylogging, often referred to as keystroke logging or keyboard capturing, is a clandestine method used by cyber attackers to monitor and record every keystroke made on a target’s device. This allows malevolent actors to stealthily gather sensitive information, including passwords, credit card numbers, and personal messages, without the user’s knowledge. Keyloggers can be introduced to a system through malicious software downloads, email attachments, or even hardware devices discreetly attached to a computer. Once activated, they operate covertly in the background, collecting data and often transmitting it to a remote hacker. The insidious nature of keylogging underscores the importance of maintaining up-to-date security software, being cautious of unfamiliar downloads, and regularly monitoring for unusual system behaviour. Staying informed and vigilant is crucial in protecting oneself from the silent threat posed by keyloggers.
The Menace of Credential Stuffing.
Credential Stuffing is a cyberattack strategy wherein attackers exploit individuals’ tendency to reuse passwords across multiple online platforms. In this method, hackers take combinations of usernames and passwords leaked from one data breach and attempt to gain access to other accounts using the same credentials. Given the vast number of breaches and the volume of exposed login details available on the dark web, attackers utilise automated tools to rapidly attempt sign-ins across various websites. Successful entries can provide unauthorised access to a plethora of sensitive accounts, from email and social media to financial services. The prevalence of credential stuffing attacks highlights the critical importance of using unique passwords for each online service and underscores the value of multi-factor authentication as an additional layer of security. Regularly updating passwords and employing password managers can also serve as effective deterrents against such invasive attacks.
Rainbow Table Attacks.
Rainbow Table Attacks present a sophisticated approach to cracking hashed passwords. In cryptography, passwords are often stored as hashes—unique sets of characters generated from the original password. Instead of attempting to decrypt these hashes directly, attackers use rainbow tables, which are precomputed tables containing hashes for a vast number of possible password combinations. By comparing the stored hash with values in the rainbow table, hackers can swiftly identify the original password. These tables expedite the cracking process, bypassing the need for time-consuming calculations. However, the effectiveness of rainbow table attacks can be significantly reduced by employing “salting” techniques, where random data is added to passwords before hashing. This addition ensures that even identical passwords produce distinct hashes, making them resistant to rainbow table comparisons. As cyber threats like these persistently evolve, the importance of advanced security measures and continuous education remains paramount.
The Consequences of a Web Security Breach.
When a website suffers a security breach, the fallout is not merely limited to short-term technical disruptions. The after-effects can ripple through various facets of your business, leaving long-lasting scars. A breach can swiftly erode the hard-earned trust and reputation of a business, sometimes causing irreversible damage to its brand image. Such incidents can lead to not only a decline in customer confidence but also tangible losses in sales and revenue. Operational hindrances might emerge, disrupting day-to-day business activities and stalling critical marketing initiatives. More alarmingly, a cyber intrusion can expose sensitive data, putting both the business and its clients at risk. Such exposures can open the door to legal actions, further escalating the crisis. Beyond the immediate ramifications, the long-term costs of reputation management, enhanced website security measures, and potential compensations make it essential for businesses to prioritise cybersecurity. By understanding the depth and breadth of potential impacts, businesses can better appreciate the importance of fortifying their digital frontiers.
Central Coast Websites prioritise the security of websites with utmost diligence, ensuring comprehensive safeguards are in place. We are committed to shielding your site and business from damaging cyber threats, offering a robust defence against potential attacks.
Website Data Loss.
One of the primary motivations behind cyberattacks is sheer malice. Perpetrators can infiltrate your website, wiping out essential data integral to its operations. This loss isn’t limited to just the site’s content; it extends to crucial transactional records, including online orders, communication emails, and invoices. Methods like brute force attacks can provide hackers unrestricted access to your server or the administrative sections of your website. Moreover, SQL injection attacks pose a risk to your databases, enabling malefactors to delete or manipulate data at will.
Damage your Trust and Reputation.
A security breach goes beyond mere technical implications. The intangible effects on a business can be profound and long-lasting. Any website downtime or anomalies can sow seeds of doubt in your customers’ minds, leading them to question the reliability of your platform. The situation becomes direr if hackers implant malicious content, such as inappropriate material, which can tarnish your brand’s image instantaneously. Rebuilding trust and restoring your brand’s reputation post such incidents can be a challenging endeavour, with some customers possibly harbouring reservations for an extended period. At Central Coast Websites, we recognise these threats and emphasise holistic security measures, ensuring your website remains impervious to potential attacks and upholds its integrity.
Unwanted Website Redirections.
Cybercriminals can manipulate your website to redirect visitors to an entirely different site. Such unauthorised redirections not only tarnish your brand’s credibility but can also derail ongoing marketing initiatives, including pay-per-click campaigns on platforms like Google Ads. We’ve encountered clients who faced such challenges, resulting in substantial financial losses. It’s imperative to be proactive and implement safeguards against these potential threats.
Restoring a Compromised Website.
Addressing the aftermath of a cyberattack and restoring a compromised website can be both challenging and costly. Malware infiltrations and other forms of cyber breaches demand meticulous repairs. With a dedicated partner like Central Coast Websites by your side, website security is a top priority. We instate multiple protective measures to preempt potential breaches. However, if your website includes user logins, it’s crucial to ensure that passwords are robust and impenetrable, bolstering your site’s resilience against potential threats.
The Importance of Having Strong Passwords.
At Central Coast Websites, our commitment to security is unwavering. As underscored in our previous discussions on website security, we implement rigorous safeguards and continuously update plugins and the WordPress platform to ensure optimal protection. However, the cornerstone of this protective framework remains a robust password, especially for users with login credentials. A potent password acts as the first line of defence, safeguarding your website from potential breaches. Should you seek guidance on fortifying your password or have queries about overall security measures, we’re here to assist.
Prioritise a strong password; it’s a simple step with profound implications for your site’s security.